CertWatch is a Firefox add-on that helps you control how digital certificates are used when you visit secure websites. While there exist tools that help control how, for example, scripts like Javascript are executed (NoScript addon), there has not been a tool for digital certificates.
The closest Firefox addon to the functionality of CertWatch is Certificate Patrol, which keeps track of website certificates and notifies when a revisited website has a different website certificate. CertWatch collects more information than Certificate Patrol and keeps track of root, intermediate and website certificates, plus visit details.
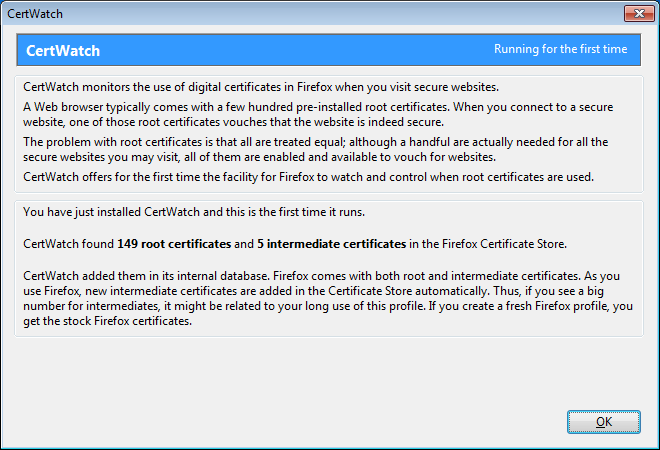
Once you install CertWatch and restart Firefox, CertWatch will take up to 30 seconds to parse all root certificates that your Firefox comes with. Every secure website that you visit is vouched for by some root certificate that pre-exists in Firefox. Your Firefox has about 150 of those root certificates, and you can traditionally view them in Edit»Preferences»Advanced»Encryption»View Certificates»Authorities.
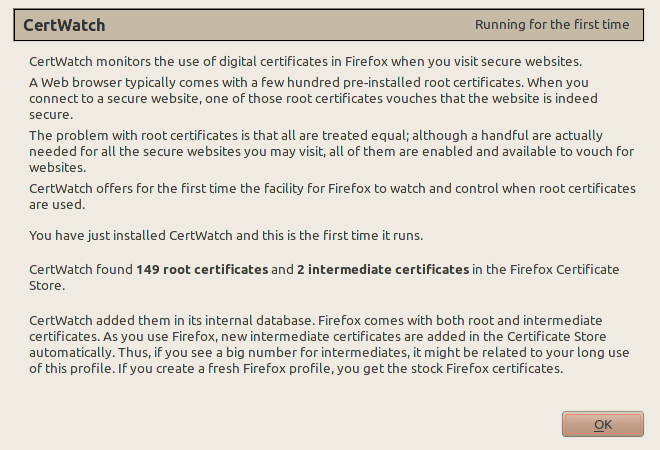
This is Firefox 4 (beta1) with a new profile. Both Firefox 4 and Firefox 3.6.8 (as found in Ubuntu 10.04) come with 149 root certificates. If you have more than 149, then you accepted yourself extra root certificates which are fully enabled and can vouch for secure websites. As you browse, your Firefox collects intermediate certificates (I plan to explain all these in future posts at certwatch.simos.info). These are added to Firefox without user interaction, as long as the respective root certificate is in Firefox as well.
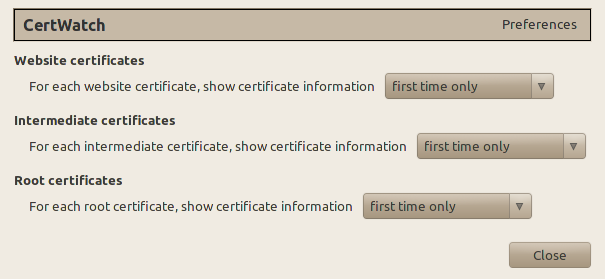
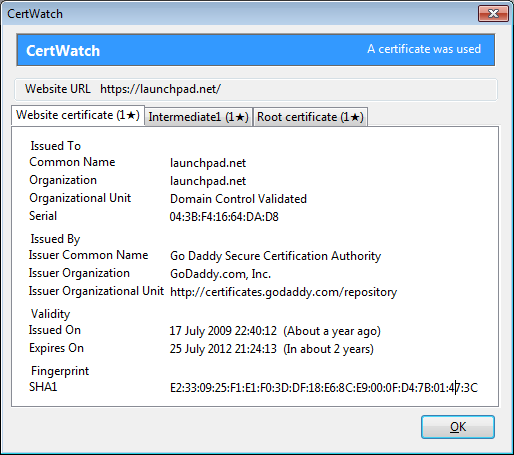
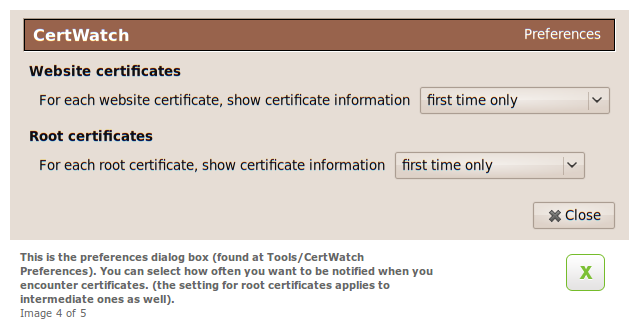
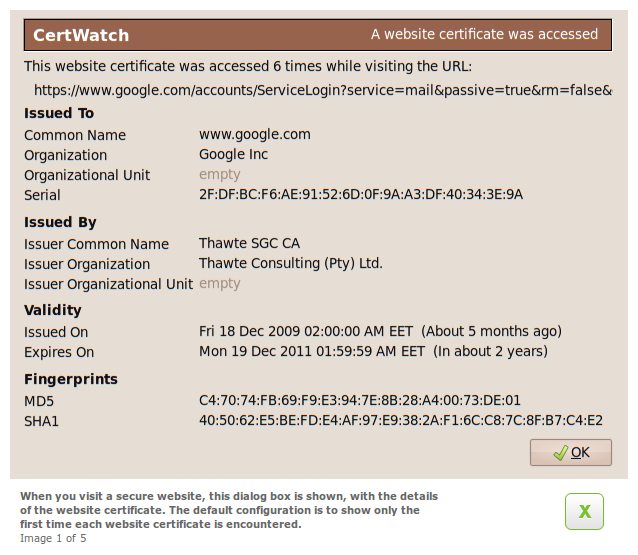
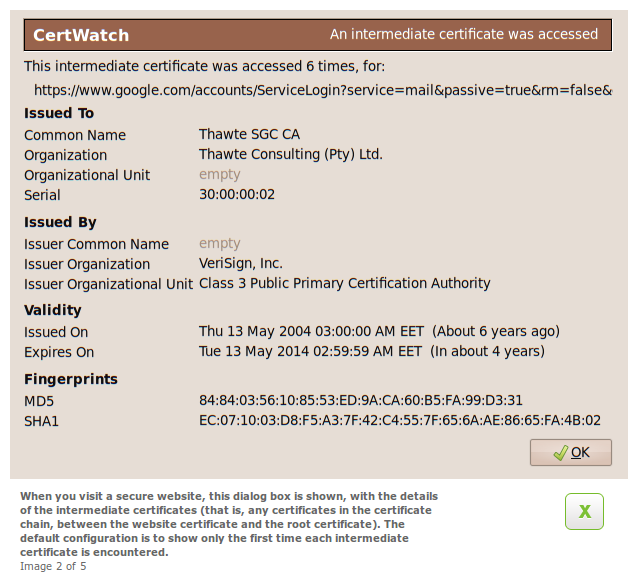
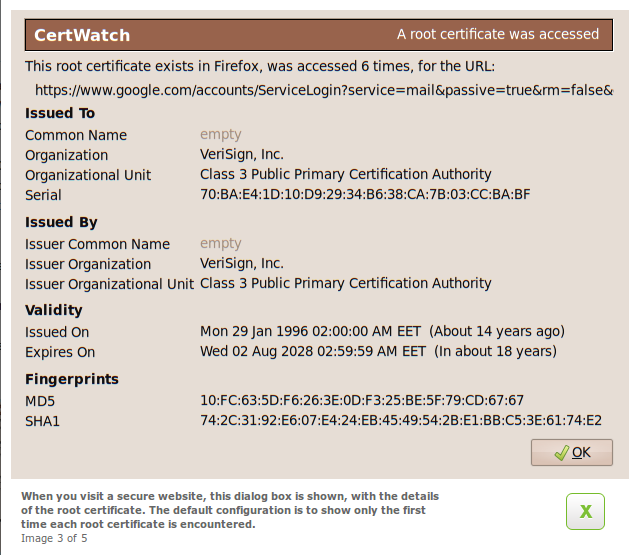
These are the preferences, accessible from Tools » CertWatch Preferences. When you visit a secure website, there is a process where the website certificate is vouched by the root certificate that Firefox already knows. Between the website and root certificates there could be intermediate certificates, creating what is called a certificate chain.
What the preferences do is specify when you should get a notification while you visit a secure website. The default preferences say that for the certificate chain of a secure website, show the certificate details if any of the website, intermediate or root certificates are encountered for the first time.
Let’s visit https://addons.mozilla.org/ with CertWatch installed.
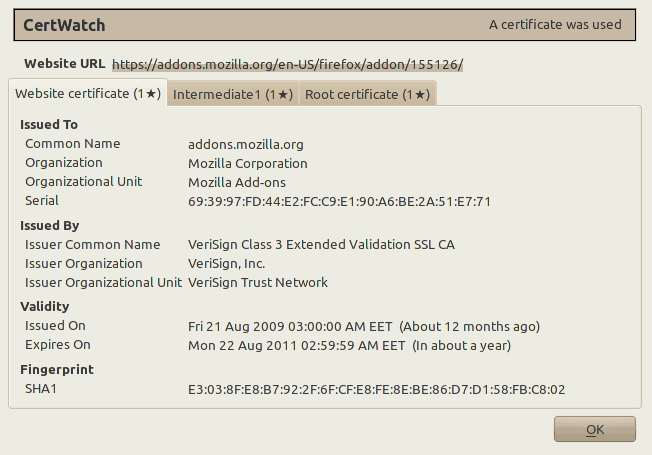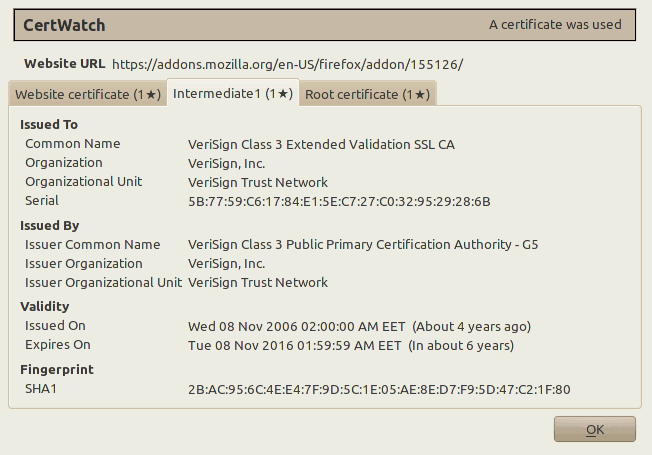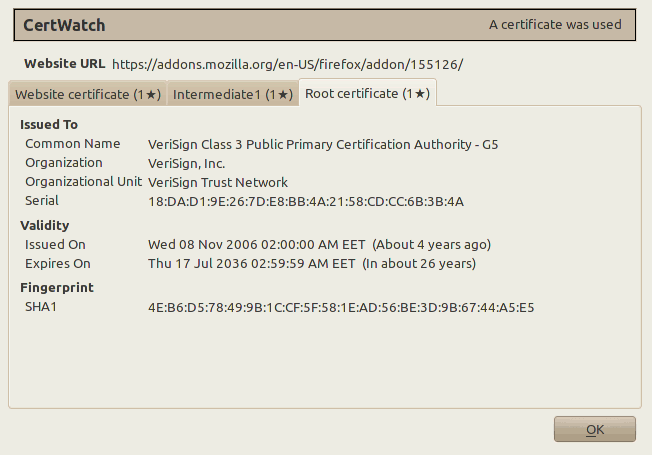
Each tab correspond to a certificate. All these three certificates are the certificate chain that verifies the secure website https://addons.mozilla.org/. The numbers at the tab names indicate how many times CertWatch encountered these certificates. It’s the first time, so they all show 1. The black star ★ indicates whether the CertWatch Preferences apply for each certificate. Since the preferences indicate first time only, then all tabs get a star.
From the list of root certificates, only a handful of them will be ever used during your browsing and with CertWatch you now have the facility to figure out which ones are actually being used. At this stage I would consider this as the first most important use of CertWatch; keeping track on how many times certificates are used. If you encounter a new certificate when you visit a revisited website, then this is something to investigate.
CertWatch keeps its copy of certificates in an SQLite database in your Firefox profile. For Linux, the path is ~/.mozilla/firefox/YOURPROFILENAME/CertWatchDB3.sqlite. You can read the database with any SQLite client such as the Firefox Addon SQLite Manager or sqlitebrowser (Packaged in Debian and Ubuntu as sqlitebrowser). In the SQLite database you can view the root/intermediate certificate table, the website certificate table, and the website visits table. In all cases the full certificate is stored in case you want to contribute to the EFF SSL Observatory.
CertWatch is developed on Ubuntu Linux 10.04, with Eclipse 3.6 (Helios) and the JSDT environment.
Install the latest version of CertWatch, which is available from the addons.mozilla.org (AMO) CertWatch page.
Follow the progress of CertWatch at the https://certwatch.simos.info/ CertWatch blog.
Here are some secure websites for testing, https://www.google.com/, https://www.paypal.com/, https://www.facebook.com/, https://twitter.com/