Certificate Watch (CertWatch) is a Firefox extension that helps detect security problems with certificates in secure websites (https://).
I uploaded CertWatch 1.0 to AMO (Addons.Mozilla.Org) and it will take a few days until it gets accepted and becomes available there.
Therefore, let’s see for now what we get with CertWatch 0.8.
Installation
You can install CertWatch 0.8 by visiting the CertWatch AMO web page.
Once you install, select to restart your browser. Note that when you restart your browser, CertWatch performs an analysis of your Firefox’s root certificates and adds them to its own copy, in the file CertWatchDB2.sqlite, in your profile folder. This analysis may take up to 30 seconds (if your computer is slow), therefore be patient.
First use
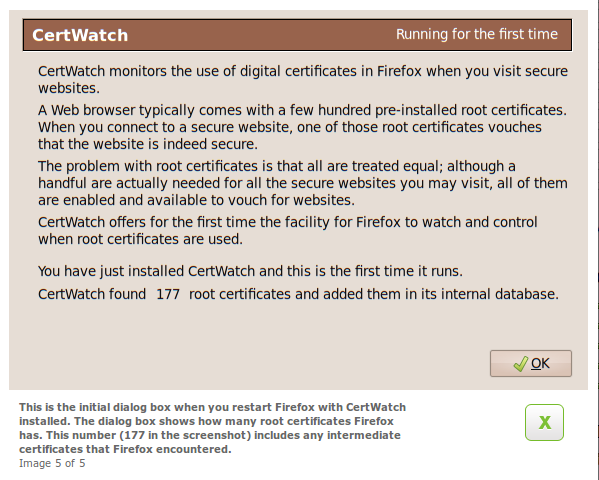
Once you have installed CertWatch 0.8 and you restart Firefox, you are presented with a dialog similar to the one above. It shows the number of root certificates (includes what we call “intermediate” certificates as well) that have been read from Firefox and saved in CertWatch’s database. In CertWatch we distinguish between root and intermediate certificates. Click OK and you are read to surf.
Preferences
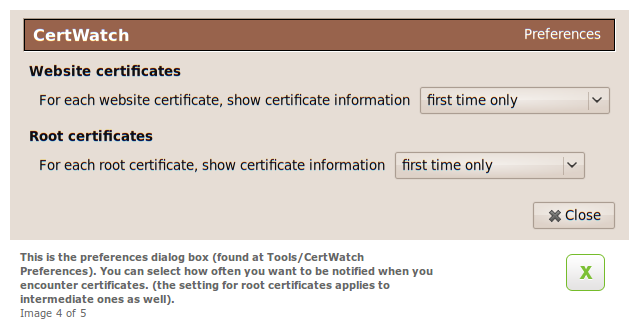
The CertWatch preferences are accessible from Tools » CertWatch Preferences.
When you visit a secure (i.e. https://) website, Firefox verifies whether the website certificate (secure websites come with “certificates”) is vouched by some authority, a Certification Authority (CA). These Certification Authorities are the 177 root certificates we saw earlier. There is a link between a website certificate and a corresponding root certificate in Firefox. In addition, between the website and root certificates there might be more certificates, the intermediate certificates. All these together make a chain.
So, when you visit a secure website, Firefox finds all the elements of the certification chain and verifies that a website is secure.
Once of the principle tasks of CertWatch is to keep track how many times a certificate has been accessed. When you repeatedly visit secure websites, the same certificates are used. So, with these preferences, CertWatch asks you how often to get notifications when certificates are accessed. The default is, when any new certificate is accessed, to show some notification.
In CertWatch 0.8 you can select up to how many times a new certificate (either website or root/intermediate) should be shown, when you visit a secure website.
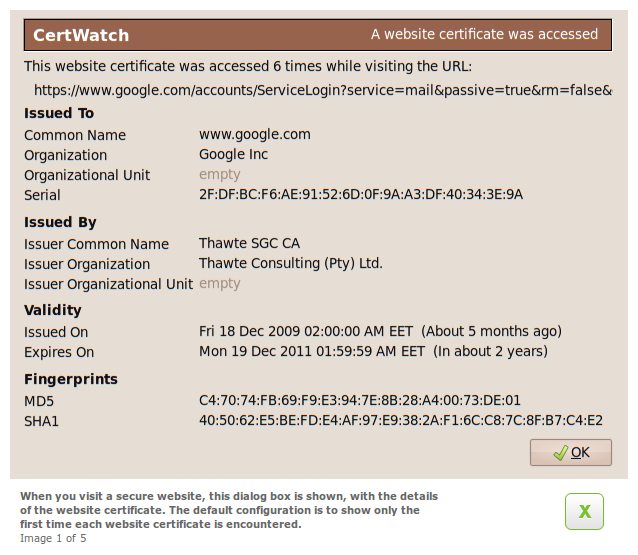
This is a website certificate; every secure website has one of those. Issued To are the details of the website according to the certificate. Issued By are the details of the certification authority that vouches for the website certificate. From these details we do not know yet whether this Thawte certificate is a root certificate or whether it’s an intermediate certificate with some other root certificate on top.
Validity shows when the certificate was issued and when it expires. I hope you like the human-readable text next to the dates. Finally, the SHA-1 fingerprint of the certificate is shown. We keep track of the fingerprints in the CertWatch database; it helps to identify if something strange changed in the chain.
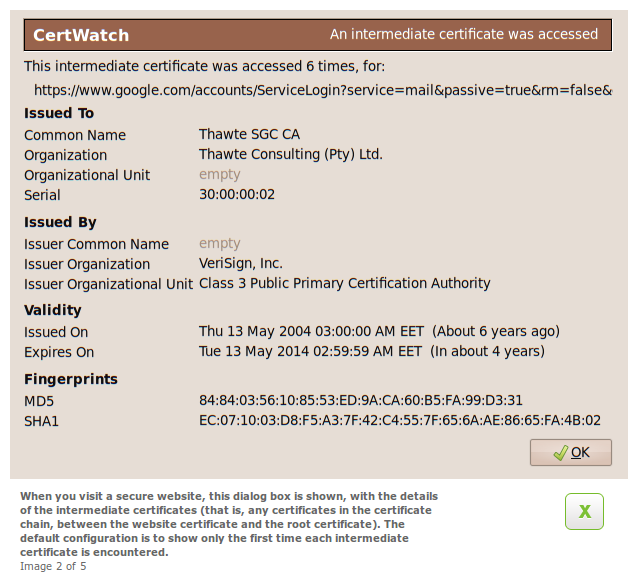
These are the details of the Thawte certificate. It is issued by a Verisign certificate so we know that the Thawte certificate is an intermediate certificate. We will see below whether the Verisign certificate is the root certificate or just an intermediate certificate.
Why does Verisign vouch for a Thawte certificate? Aren’t they different companies? Thawte was a South African company by Mark Shuttleworth (Ubuntu fame, cosmonaut) who sold his company in 1999 to Verisign. Now Thawte is part of Verisign.
You can notice the validity, compared to the validity of the website certificate. The more we move towards the root certificate, the validities become wider (compare two years to ten years for website and intermediate respectively).
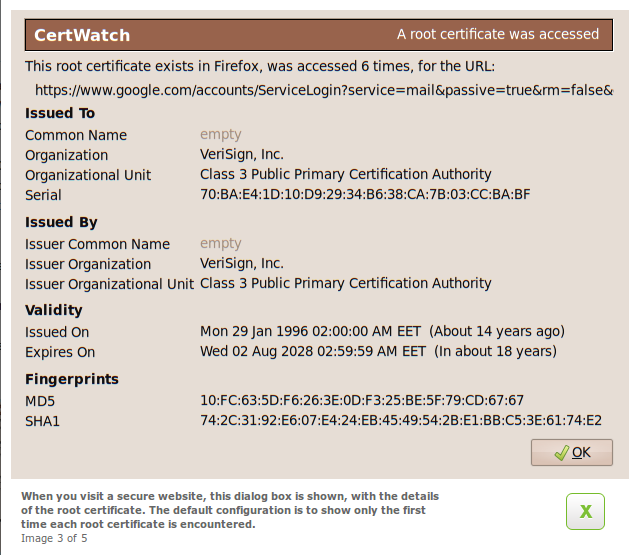
This is the root certificate. The Issued To and Issued By details are the same. In CertWatch 1.0 this detail will be more visual than having to compare strings.
Although this certificate is for Google (I am insinuating quality), it is amazing how old the certificate is. It hails from 1996. The validity span is over 30 years. A piece of information that we do not show yet in CertWatch is the key size; this Verisign certificate from 1996 has a key size of 1024 bits. If you read the security news, you may have noticed complaints about this root certificate. It gets a bit worse; both this Verisign and the Thawte certificates have 1024-bit keys.
Are these two 1024-bit keys compromised? We can only speculate at this time. It will helps us figure out the answer if we can find out, how much harder it is to perform calculations between 1024-bit and 2048-bit RSA keys, and multiply that with the millions that connect to Google and GMail every day. If the computation requirements are not very different between the two, then there is no reason to keep 1024-bit keys.
